Here's what we're covering in this guide.
- PART 1: Internal documentation systems (SOPs, ops docs)
- PART 2: Core workflows for operations and project management (projects, OKRs)
- PART 3: Permissions and security
- PART 4: Automations and integrations
How to use Notion for security & permissions
As we’ve discussed throughout this guide, Notion is purposely open and flexible by default. Without some guardrails, that openness can become a liability, fast!
On the free plan, every member is a Workspace Owner, meaning they have full control over everything, including billing. That setup makes sense for individual users, but most teams start on the free plan and never revisit those settings when they upgrade. As a result, critical admin privileges and visibility remain widely available across the entire team even as teams scale, often without anyone realizing it, causing a security risk.
That level of freedom creates shadow systems, exposes sensitive content, and leads to a flood of disconnected spaces no one’s responsible for.
Security isn’t just about who can edit a doc and view sensitive information - it’s about who can create new systems, who controls the visibility of sensitive data that not all employees (and especially not people outside the company) should see, and who’s responsible for maintaining structure. It’s about giving the right people the right access, with the least amount of friction, all while keeping your data secure and having clear oversight over who can see what.
What all teams need to know
No matter the size of your company, a few foundational security practices go a long way, especially once you're on a paid plan with access to workspace-level admin tools:
- Use permission groups: Assign permissions to user groups in Notion (e.g. Marketing, Finance, Product) rather than managing access one person at a time. It’s faster, cleaner, and scales better.
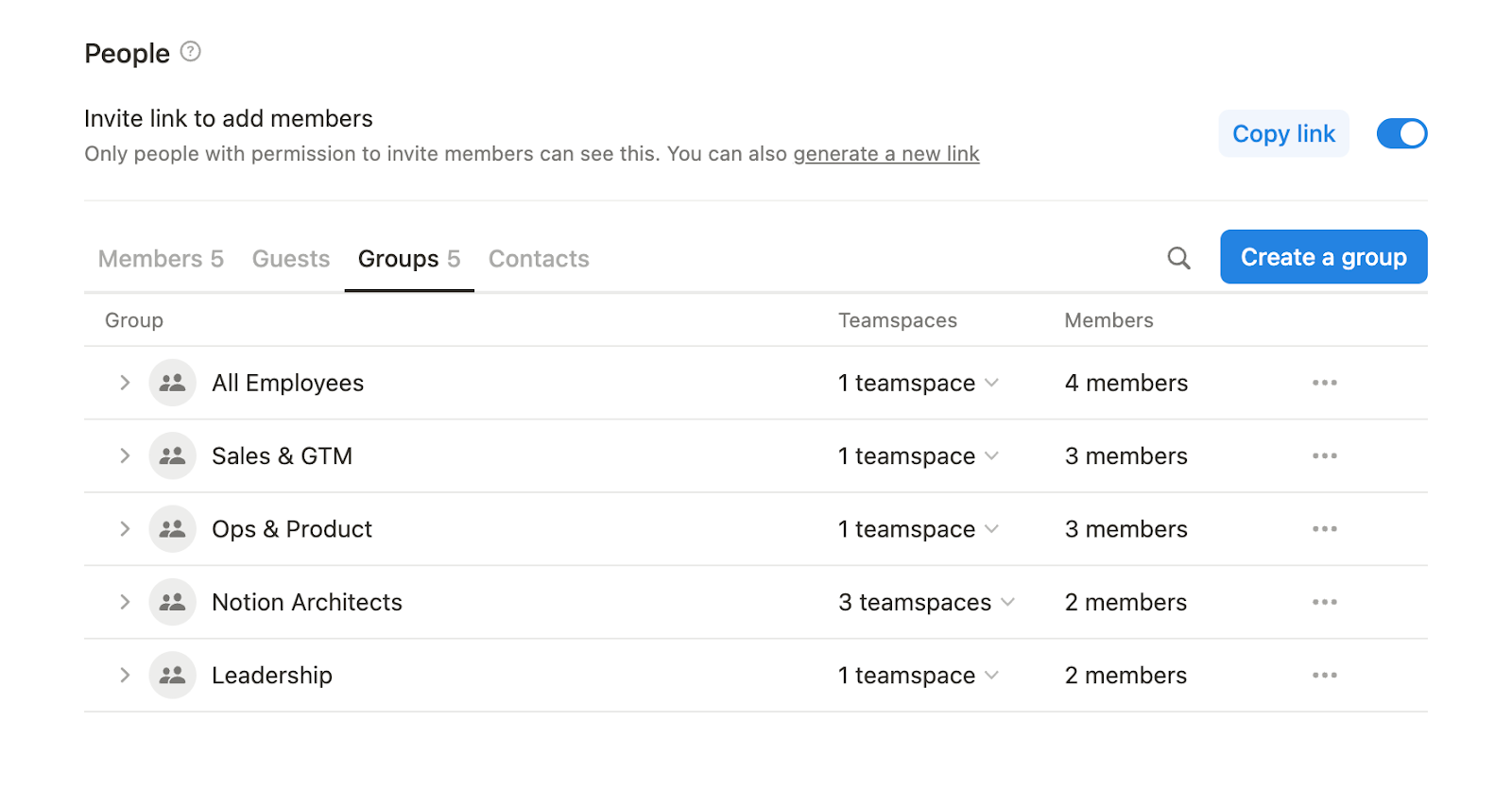
- Limit Workspace Owners: Most organizations - even at the enterprise level - don’t need more than a handful of Workspace Owners. These users have elevated permissions at the org level, including access to billing, organization-wide admin settings, and other features like security controls, data retention, and integration management. Since these settings aren’t touched often, there’s no reason to have more than a few trusted owners in charge. Fewer owners mean fewer chances for accidental (or unnecessary) changes.
- Restrict Teamspace creation: Teamspaces help organize operations and manage sensitive content, but when everyone can create them, they quickly clutter the sidebar and fragment your systems. Limit creation to Workspace Owners to prevent sprawl and maintain consistency.
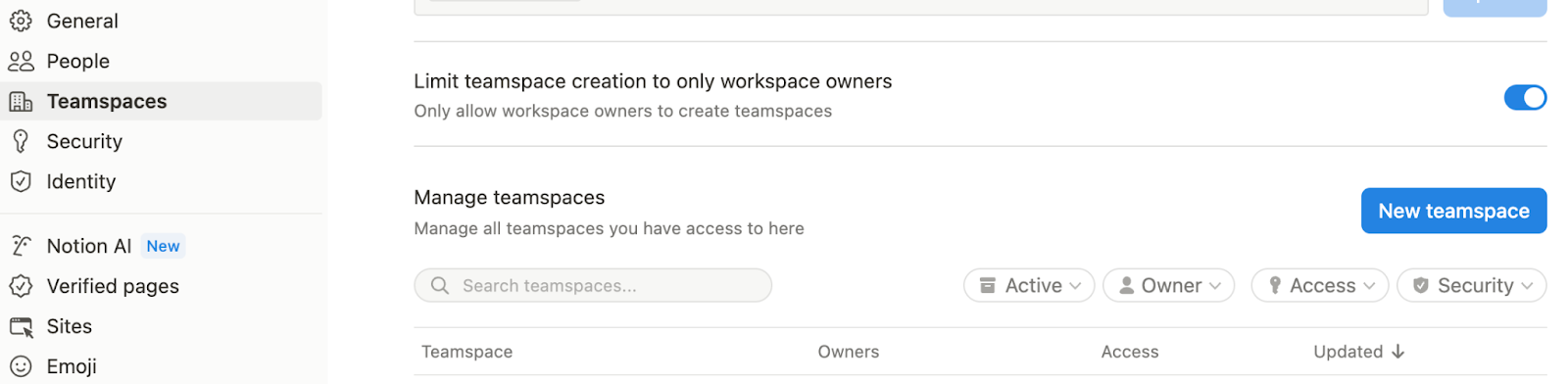
- Minimize full access. Most users don’t need full editing rights. Default to view or comment access - especially for evergreen systems (like the Company wiki) - and only grant edit access where direct engagement with content is required. Full access should only be granted to users who manage architecture.
- Define clear ownership: Every system or shared space should have an assigned owner. In small teams, this might be one person. In larger orgs, each department or hub may need its lead to manage structure, access, and content quality.
These are simple practices, but they prevent major headaches later on.
Team-specific advice
Small Teams: Start small, but be intentional when establishing permissions
When you’re moving fast, it’s easy to treat permissions as an afterthought. Everyone has full access, everyone’s building, and there’s no real separation between experimentation and core systems. And that works - until it doesn’t.
Small teams often lean hard into autonomy and creativity, but without a lightweight security structure, it’s just as easy to overwrite someone’s work as it is to contribute to it. One misplaced database, one teamspace spun up in isolation, and suddenly your ‘move fast’ culture turns into a cleanup job.
This is the moment to define enough structure to avoid chaos later:
- Follow good practices, outlined above.
- Choose one Workspace Owner who will manage workspace settings and architecture
- Build a single ‘Company’ teamspace
- Define permission groups. Two should be plenty at the beginning - ‘All Employees’ and ‘Notion Architects’. Use these two groups to manage permissions in the ‘Company’ teamspace.
You don’t need enterprise controls - you just need clarity. Hey, you can even define these rules using in your Notion wiki! See our Documentation systems guide in Part 1. Start with thoughtful defaults now, and your future self (and your growing team) will thank you.
SMBs: Introduce structure and tighter controls through intentionally organized teamspaces and permissions
At this stage, companies begin feeling the real pain of poor permission hygiene if they haven’t been following good practices. If you haven’t already, implement the good practices outlined above and clean up your workspace of redundancy and security concerns.
Most companies introduce SSO tools like Okta at this stage and nominate a few IT or operations champions to manage permissions and policies in Notion.
At this point, it also makes sense to begin aligning teamspaces and permission groups with departments (e.g., Marketing, Sales, HR). The goal here is structure without friction, so don’t overdo it - establish clear Teamspace structure and ownership, and just enough control to keep the system scalable. Define clear governance for how your organization uses Teamspaces — write it down (ideally in your Notion wiki), and make sure it’s followed. Having this documented (and enforced) helps prevent sprawl, reduces confusion, and ensures consistency as new people join or teams evolve.
A few key elements to cover in your guidelines:
- Teamspace organization: How are Teamspaces grouped - by department, function, or another model? Department is the most common aggregation point.

- Creation rules: When should new Teamspaces be created, and who’s allowed to create them? As explained earlier, we recommend limiting creation to Workspace Owners unless there’s a clear reason to expand access.
- Ownership model: How many owners should each Teamspace have? For small teams (up to 10 people), one owner is usually enough. For larger teams, 2–3 owners may be appropriate, but rarely more.
- Permission levels: Define who gets what level of access:
- Owners: Usually full access to manage structure and permissions
- Teamspace members: Usually edit access to contribute and collaborate on data
- General access: organization-wide access. This will usually be ‘can view’, ‘can comment’, or ‘no access’, depending on the sensitivity of the content inside.
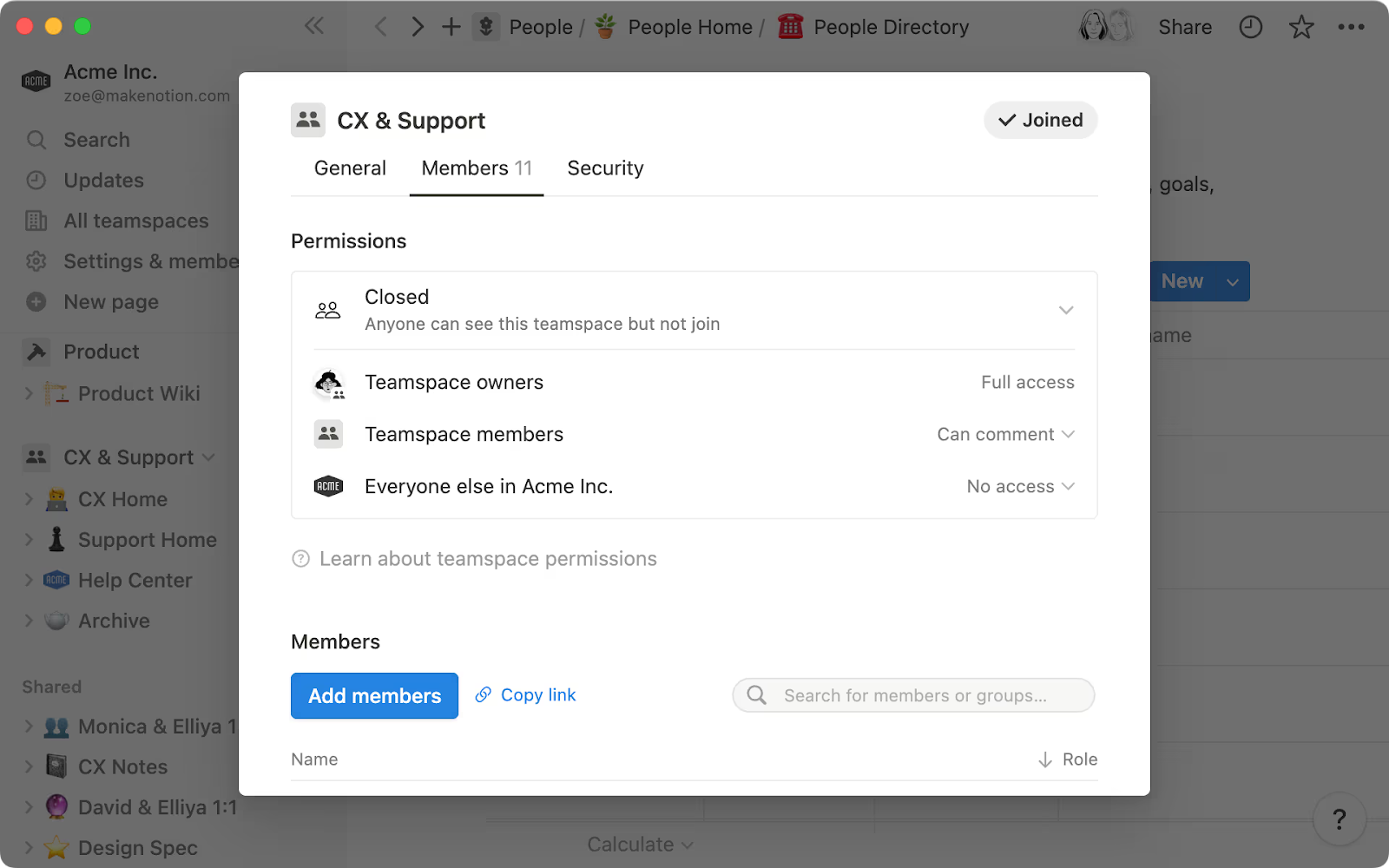
Teamspace strategy becomes critical here. Avoid over-creating Teamspaces - not every team needs their own space. Unless you need permission separation, more teamspaces mean more friction. They clutter the sidebar, fragment information, and degrade UX across altitudes. Department-specific teamspaces are the perfect level of granularity to reduce sidebar noise and keep navigation sane.
Fewer, well-governed Teamspaces mean a better UX and stronger adoption across the org. Make sure to align permission groups on the same altitude level.
Enterprises: Security becomes infrastructure
At enterprise scale, security and governance are formalized. Workspace-level access is controlled by IT and typically integrated with tools like SAML, SCIM, or enterprise-grade SSO.
But ownership can’t live in the IT department alone - not with the volume of users and complexity of org structure. Department trailblazers - often ops leads or power users within departments - take responsibility for maintaining the Notion system architecture and content quality within their teams. That said, Teamspace permissions should still be managed centrally through IT and permission groups to maintain control and consistency.
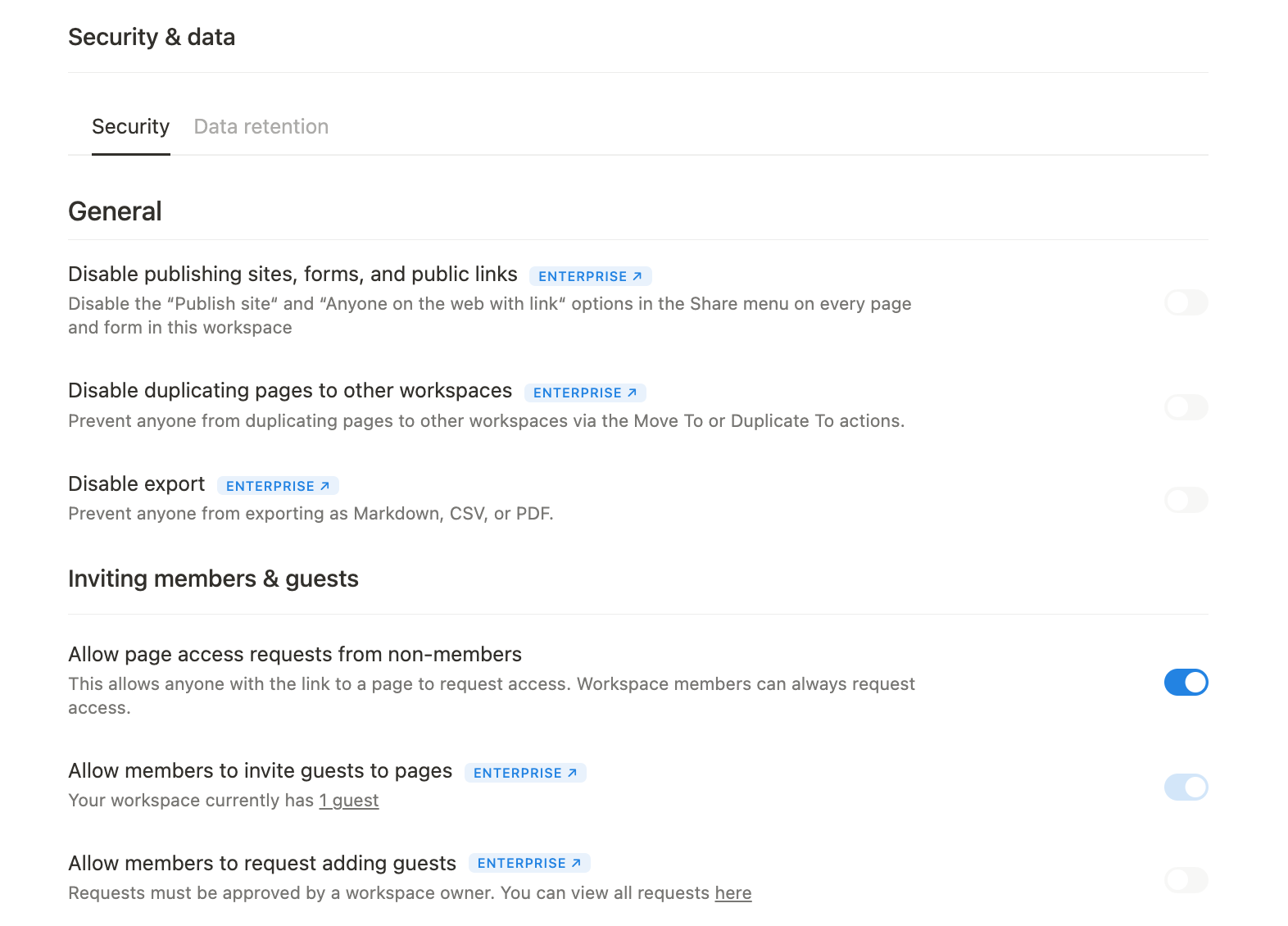
Don’t overlook the value of enterprise-level controls. They’re one of the key reasons to upgrade to Enterprise. Features like advanced data retention policies (up to 10 years), external sharing restrictions, and the ability to disable exports, guest invites, and public sharing give IT the tools needed to protect sensitive data at scale. If you're on the enterprise plan, use it to its fullest.
Conclusion
Strong permissions and security practices are what turn Notion from a flexible collaboration tool into reliable company infrastructure. By putting guardrails in place early - whether that’s a single owner and simple groups for small teams, structured teamspaces and tighter controls for SMBs, or enterprise-grade governance integrated with IT systems - you reduce risk, prevent sprawl, and keep sensitive data safe without blocking collaboration. With permissions handled, we’re ready to look at the final layer of using Notion to the best of its ability, in part 4 of this guide: Automation and Integrations.
If you haven’t already, check out Part 1 (Documentation Systems) and Part 2 (Core Workflows) of our guide on how to best build in - and get the most out of - Notion. For a more general overview of Notion and what it has to offer, check out our ‘What is Notion’ article!
Want to learn more about internal tools and how to build them? Check out our sections on low-code tools like Notion and Airtable, or developer tools like Retool and Windmill.